Exploring the realm of data security in cloud storage, this introduction sets the stage for a deep dive into the importance of safeguarding sensitive information. As businesses increasingly rely on cloud services, the risks of data breaches loom large, making it vital to understand the measures needed to protect valuable data.
In this guide, we will delve into the significance of strong authentication, encryption practices, and the necessity of regular monitoring and auditing in maintaining the security of data stored in the cloud.
Understand the Importance of Data Security in Cloud Storage
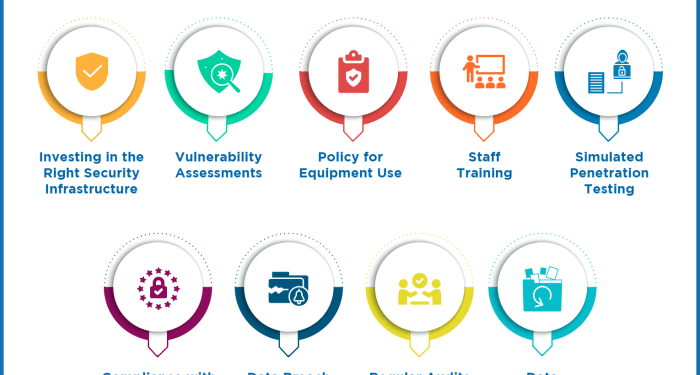
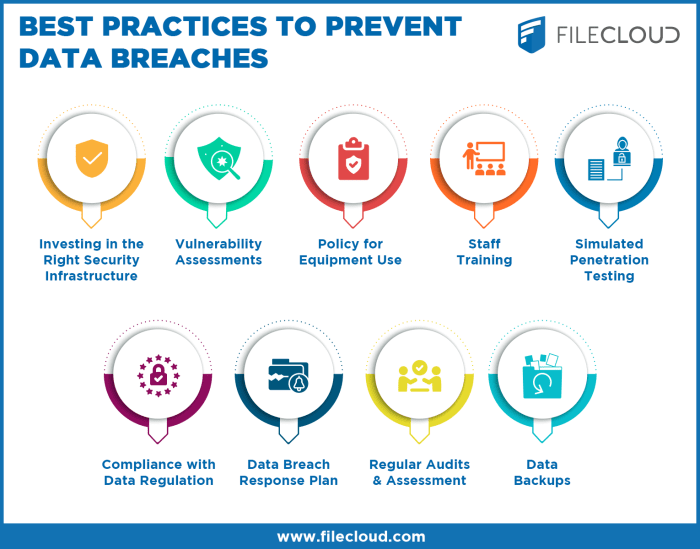
Data security in cloud storage is a critical aspect that businesses cannot afford to overlook. The risks associated with data breaches in cloud storage are significant and can have severe consequences if not properly addressed.
Risks of Data Breaches
- Data breaches in cloud storage can lead to unauthorized access to sensitive information, such as customer data, financial records, and intellectual property.
- Malicious actors can exploit vulnerabilities in cloud storage systems to steal data, causing reputational damage and financial losses for businesses.
- Data breaches can also result in legal repercussions, with companies facing lawsuits, regulatory fines, and compliance issues.
Consequences of Data Breaches
- Loss of customer trust and loyalty due to the exposure of confidential information can be detrimental to a business's reputation and bottom line.
- Financial implications, including the cost of investigating and mitigating the breach, as well as potential legal fees and fines, can be substantial.
- Data breaches can disrupt business operations, leading to downtime, loss of productivity, and damage to relationships with clients and partners.
Importance of Data Security for Businesses
- Ensuring data security in cloud storage is essential for maintaining the confidentiality, integrity, and availability of sensitive information.
- Compliance with data protection regulations, such as GDPR and HIPAA, is crucial to avoid legal consequences and protect customer data.
- Implementing robust security measures in cloud storage helps businesses safeguard their intellectual property, trade secrets, and other valuable assets against cyber threats.
Implement Strong Authentication and Access Control Measures
Implementing strong authentication and access control measures is crucial in maintaining the security of data stored in the cloud. These measures help prevent unauthorized access to sensitive information, reducing the risk of data breaches.
Role of Authentication in Preventing Unauthorized Access
Authentication plays a key role in verifying the identity of users and ensuring that only authorized individuals have access to data. By requiring users to authenticate themselves through credentials such as passwords, biometrics, or security tokens, organizations can create an additional layer of security to protect their data.
Importance of Multi-Factor Authentication
Multi-factor authentication (MFA) adds an extra level of security by requiring users to provide two or more forms of verification before accessing data. This could include something they know (like a password), something they have (like a security token), or something they are (like a fingerprint).
Implementing MFA in cloud storage significantly reduces the risk of unauthorized access, as even if one form of authentication is compromised, the additional factors provide added protection.
Significance of Access Control Mechanisms
Access control mechanisms help organizations manage and restrict user access to specific data based on predefined policies. By setting permissions and roles, organizations can ensure that users only have access to the data necessary for their roles, reducing the likelihood of data exposure or unauthorized modifications.
Implementing access control mechanisms in cloud storage environments is essential for maintaining data security and preventing unauthorized access.
Encrypt Data for Enhanced Security
When it comes to protecting data stored in the cloud, encryption plays a crucial role in ensuring enhanced security. By encrypting data, you are essentially converting the information into a code that can only be decoded with the right encryption key.
This adds an extra layer of protection, making it much harder for unauthorized users to access sensitive data.
Different Encryption Methods
- Symmetric Encryption: In this method, the same key is used for both encryption and decryption. It is efficient for large amounts of data but requires secure key management.
- Asymmetric Encryption: Also known as public-key encryption, this method uses a pair of keys - public and private. The public key is used for encryption, while the private key is used for decryption.
- End-to-End Encryption: This method ensures that data is encrypted from the sender's end and only decrypted by the intended recipient, minimizing the risk of interception.
Importance of Encrypting Data in Transit and at Rest
Encrypting data both in transit (when it is being transferred between devices or networks) and at rest (when it is stored in the cloud) is essential for maintaining the security of your information.
Encrypting data in transit protects it from being intercepted by cybercriminals during transmission, ensuring that even if intercepted, the data remains unreadable without the encryption key.
Encrypting data at rest safeguards it from unauthorized access while stored in the cloud servers. This prevents potential breaches and ensures that even if the storage is compromised, the encrypted data remains secure.
Regularly Monitor and Audit Cloud Storage Systems
Monitoring and auditing cloud storage systems are crucial aspects of ensuring data security and preventing potential security threats. By regularly monitoring these systems, organizations can proactively detect any suspicious activities or unauthorized access attempts, allowing them to take immediate action to mitigate risks.
Conducting regular audits helps in identifying vulnerabilities in the cloud storage environment. It enables organizations to assess the effectiveness of their security measures, policies, and procedures, making it easier to address any weaknesses before they are exploited by cyber attackers.
Benefits of Monitoring Cloud Storage Systems
- Early detection of security breaches or unauthorized access attempts.
- Improved incident response capabilities.
- Enhanced visibility into the cloud storage environment.
- Ensuring compliance with data protection regulations.
Best Practices for Monitoring and Auditing Cloud Storage Systems
- Utilize automated monitoring tools to continuously track activities and analyze logs for any anomalies.
- Implement real-time alerts for unusual behavior or potential security incidents.
- Regularly review access logs and user activities to detect any unauthorized access attempts.
- Conduct periodic security assessments and penetration testing to identify and address vulnerabilities.
Final Summary
In conclusion, safeguarding data in cloud storage environments is not merely a matter of choice but a critical necessity in today's digital landscape. By implementing robust security measures and staying vigilant against potential threats, businesses can mitigate the risks of data breaches and uphold the integrity of their sensitive information.
FAQ
What are the potential consequences of a data breach in cloud storage?
The consequences can range from financial losses and reputational damage to legal implications and loss of customer trust. It's essential to take preventive measures to avoid such outcomes.
Why is multi-factor authentication important in cloud storage?
Multi-factor authentication adds an extra layer of security by requiring users to provide multiple credentials to access data, reducing the risk of unauthorized access in case one factor is compromised.
How can encryption help protect data stored in the cloud?
Encryption converts data into a secure format that can only be accessed with the right decryption key, ensuring that even if data is intercepted, it remains unreadable to unauthorized parties.
What are the benefits of monitoring cloud storage systems for security threats?
Monitoring helps detect unusual activities, unauthorized access attempts, or potential breaches early on, allowing for timely intervention to prevent data compromise.
What are the best practices for auditing cloud storage systems effectively?
Regular audits involve reviewing access logs, permissions, and configurations to identify vulnerabilities, misconfigurations, or compliance issues that could pose security risks.