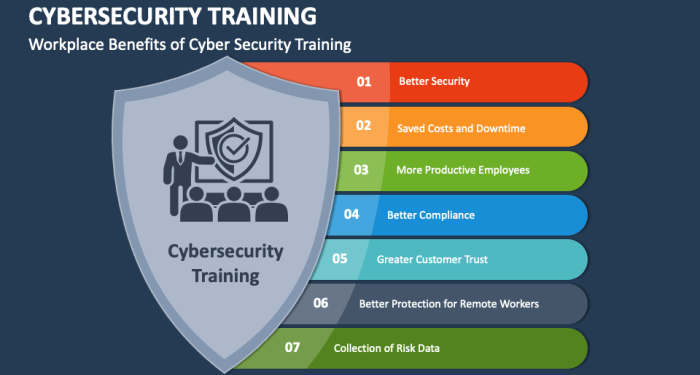
Starting with the significance of cybersecurity training for employees, the narrative unfolds in a compelling and distinctive manner, drawing readers into a story that promises to be both engaging and uniquely memorable.
Exploring the potential risks, threats, and impacts of cyber attacks on untrained employees creates a sense of urgency for organizations to prioritize cybersecurity training.
Importance of Cybersecurity Training for Employees

Cybersecurity training for employees is crucial in any organization to ensure the protection of sensitive data and prevent cyber threats. Without proper training, employees may unknowingly engage in risky behavior that could compromise the security of the company.
Identifying Potential Risks and Threats
Effective cybersecurity training can help mitigate various risks and threats that organizations face, including:
- Phishing attacks: Employees may fall victim to phishing emails, leading to unauthorized access to company systems and data.
- Malware infections: Clicking on malicious links or downloading attachments can result in malware infections that disrupt operations and compromise data.
- Social engineering: Cybercriminals may manipulate employees into divulging sensitive information through social engineering tactics.
- Data breaches: Lack of awareness about data security practices can result in data breaches that expose confidential information.
Impact of Cyber Attack on Untrained Employees
In the event of a cyber attack, a company that lacks trained employees may face severe consequences, including:
- Financial losses: Cyber attacks can lead to financial losses due to data theft, downtime, and recovery costs.
- Damaged reputation: A breach resulting from employee negligence can tarnish the company's reputation and erode customer trust.
- Legal implications: Non-compliance with data protection regulations due to employee errors can result in legal penalties and fines.
- Operational disruptions: A cyber attack can disrupt normal business operations, leading to productivity losses and service disruptions.
Types of Cybersecurity Training Programs

When it comes to cybersecurity training programs for employees, there are various types available to suit different learning styles and needs. Let's compare and contrast some of these options to understand their benefits.
Hands-on Training vs. Theoretical Training
Hands-on training in cybersecurity involves practical exercises and simulations that allow employees to apply their knowledge in real-world scenarios. This type of training helps individuals develop skills that are directly applicable to their job roles and responsibilities. On the other hand, theoretical training focuses on teaching the concepts, principles, and best practices of cybersecurity without practical application.
- Hands-on Training:Examples of hands-on training include simulated phishing attacks, penetration testing exercises, and incident response simulations. These activities give employees the opportunity to practice identifying and responding to cyber threats in a controlled environment.
- Theoretical Training:Theoretical training may include online courses, webinars, and lectures that cover topics such as cybersecurity fundamentals, threat intelligence, and compliance regulations. While theoretical training provides a solid foundation of knowledge, it may not be as effective in preparing employees to handle real-world cyber threats.
Interactive Cybersecurity Training Methods
Interactive cybersecurity training methods combine elements of hands-on and theoretical training to create engaging and effective learning experiences for employees. These methods often incorporate gamification, simulations, and case studies to help employees develop practical skills while reinforcing theoretical knowledge.
- Benefits of Interactive Training:
- Enhanced Engagement: Interactive training keeps employees engaged and motivated to learn, leading to better retention of information.
- Real-World Application: By simulating realistic scenarios, interactive training helps employees practice their cybersecurity skills in a safe environment.
- Immediate Feedback: Interactive training provides instant feedback on performance, allowing employees to learn from their mistakes and improve their skills.
- Adaptability: Interactive training can be tailored to the specific needs and skill levels of employees, ensuring a personalized learning experience.
Key Components of Effective Cybersecurity Training
Effective cybersecurity training programs should encompass a variety of essential elements to ensure that employees are equipped with the knowledge and skills needed to protect sensitive information and prevent cyber threats. Designing a comprehensive training curriculum that covers topics such as phishing awareness, data protection, and password management is crucial in fostering a culture of cybersecurity within an organization.
Additionally, organizing practical cybersecurity training sessions for employees can help reinforce key concepts and provide hands-on experience in dealing with potential security incidents.
Phishing Awareness
- Definition of phishing and common phishing techniques
- How to identify phishing emails and messages
- Best practices for avoiding falling victim to phishing attacks
- Simulated phishing exercises to test employees' awareness
Data Protection
- Understanding the importance of data protection
- Types of sensitive data and how to handle them securely
- Encryption methods and data security protocols
- Procedures for reporting data breaches or security incidents
Password Management
- Creating strong and unique passwords
- Implementing multi-factor authentication for enhanced security
- Regularly updating and changing passwords
- Recognizing the risks of password sharing or reuse
Implementing Cybersecurity Training in the Workplace

Implementing cybersecurity training within an organization is crucial to protect sensitive data and prevent cyber threats. Here are some strategies to effectively implement cybersecurity training in the workplace:
Create a Culture of Cybersecurity Awareness
Encourage a culture of cybersecurity awareness by organizing regular training sessions, workshops, and seminars to educate employees about the importance of cybersecurity. Emphasize the role each employee plays in maintaining the security of the organization's data.
Provide Hands-On Training
Offer hands-on training sessions where employees can practice identifying and responding to potential security threats in a simulated environment. This interactive approach can help employees better understand cybersecurity concepts and best practices.
Utilize Phishing Simulations
Conduct phishing simulation exercises to test employees' ability to recognize phishing emails and other social engineering tactics. Provide immediate feedback to employees who fall for simulated phishing attacks to help them learn from their mistakes.
Regularly Update Training Materials
Ensure that cybersecurity training materials are regularly updated to reflect the latest cyber threats and security best practices. By keeping the content current, employees will be better prepared to defend against evolving cyber threats.
Measure the Effectiveness of Training
Implement pre- and post-training assessments to measure the effectiveness of cybersecurity training programs. Monitor key performance indicators such as the number of security incidents reported by employees and the overall cybersecurity posture of the organization.
Last Point
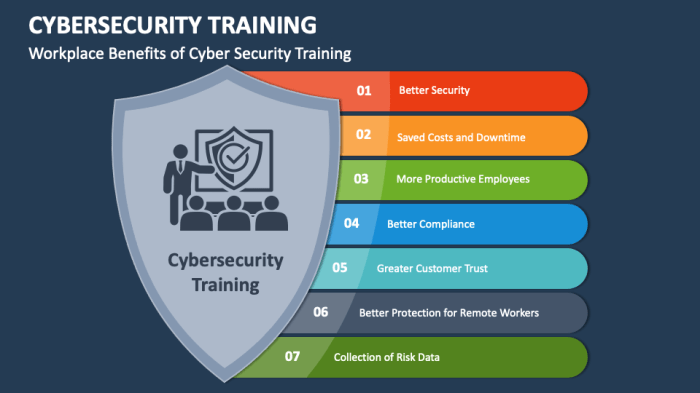
In conclusion, cybersecurity training for employees is not just a necessity but a strategic investment in safeguarding company data and operations. By fostering a culture of awareness and preparedness, businesses can effectively combat cyber threats in an ever-evolving digital landscape.
Common Queries
Why is cybersecurity training important for employees?
Cybersecurity training is crucial to equip employees with the knowledge and skills needed to identify and mitigate potential cyber threats, safeguarding the company's data and systems.
What are the benefits of interactive cybersecurity training methods?
Interactive training methods engage employees more effectively, making the learning experience more memorable and impactful. They can simulate real-world scenarios and help employees develop practical skills in handling cyber threats.
How can organizations measure the effectiveness of cybersecurity training programs?
Organizations can measure the effectiveness of training programs by tracking metrics such as the reduction in successful phishing attempts, increased employee awareness of cybersecurity best practices, and improved response times to potential threats.