In today's digital age, the convenience of public Wi-Fi networks has become a staple for staying connected on the go. However, with this convenience comes a lurking danger - security risks that threaten the safety of your personal information. Let's delve into the realm of public Wi-Fi networks and explore the measures you can take to protect yourself from potential cyber threats.
As we navigate through the different types of security risks, methods to mitigate them, and the importance of secure browsing habits, you'll gain valuable insights to ensure a safer online experience while using public Wi-Fi networks.
Introduction to Public Wi-Fi Networks Security Risks
Public Wi-Fi networks are wireless networks that are accessible to the public in places like coffee shops, airports, hotels, and libraries. These networks allow users to connect to the internet without needing a password or any special permission.
The popularity of public Wi-Fi networks has grown significantly in recent years due to the convenience they offer. People can easily access the internet on their smartphones, tablets, and laptops while on the go, without using their cellular data.
Inherent Security Risks of Public Wi-Fi Networks
When using public Wi-Fi networks, there are several security risks that users need to be aware of:
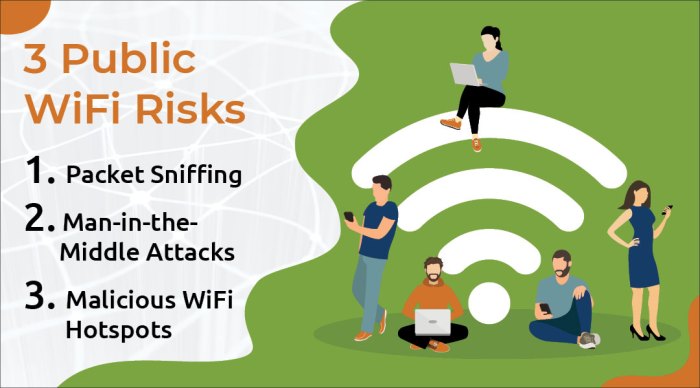
- Man-in-the-Middle Attacks:Hackers can intercept the communication between a user's device and the Wi-Fi network, allowing them to steal sensitive information such as login credentials, financial details, and personal data.
- Unencrypted Connections:Public Wi-Fi networks often lack encryption, making it easier for hackers to eavesdrop on the data being transmitted between the user's device and the network.
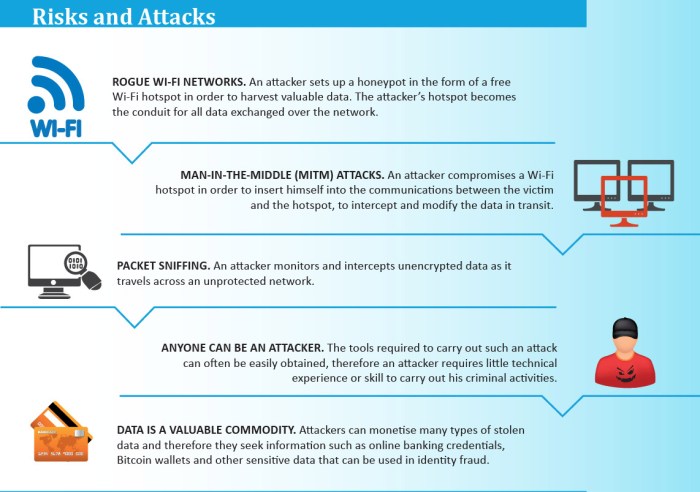
- Rogue Hotspots:Cybercriminals can set up fake Wi-Fi networks that mimic legitimate ones, tricking users into connecting to them and giving hackers access to their data.
- Malware Distribution:Public Wi-Fi networks can be a breeding ground for malware, as hackers can inject malicious software into the network and infect the devices of unsuspecting users.
Types of Security Risks on Public Wi-Fi Networks
Public Wi-Fi networks pose various security risks that users should be aware of to protect their sensitive information.
Man-in-the-Middle Attacks
One common threat on public Wi-Fi networks is the Man-in-the-Middle (MitM) attack, where a cybercriminal intercepts communication between two parties without their knowledge. This allows the attacker to eavesdrop on sensitive information such as login credentials, financial details, or personal data.
Malware Distribution
Another risk is the distribution of malware through public Wi-Fi networks. Attackers can inject malware into users' devices by exploiting vulnerabilities in the network, leading to data breaches, identity theft, or financial loss.
Wi-Fi Phishing
Wi-Fi phishing is a type of attack where cybercriminals set up fake Wi-Fi networks that mimic legitimate ones to trick users into connecting. Once connected, the attackers can capture sensitive information like usernames, passwords, and credit card details entered by unsuspecting users.
Session Hijacking
Session hijacking occurs when an attacker steals a user's session token to impersonate them and gain unauthorized access to sensitive accounts or data. This can happen on public Wi-Fi networks where user sessions are not properly encrypted, leaving them vulnerable to exploitation.
Methods to Mitigate Security Risks on Public Wi-Fi Networks
When using public Wi-Fi networks, it is crucial to take steps to protect your data from potential security risks. Here are some best practices to stay safe:
Use of Virtual Private Networks (VPNs) for Added Security
One of the most effective ways to enhance security on public Wi-Fi networks is by using a Virtual Private Network (VPN). A VPN creates a secure, encrypted connection between your device and the internet, making it difficult for hackers to intercept your data.
Encryption Protocols for Data Protection
Implementing encryption protocols can help safeguard your data while using public Wi-Fi networks. Encryption scrambles your data, making it unreadable to anyone trying to intercept it. Always ensure that websites you visit are encrypted with HTTPS to add an extra layer of protection.
Importance of Secure Browsing Habits on Public Wi-Fi Networks
When using public Wi-Fi networks, it is crucial to practice secure browsing habits to protect your sensitive information from potential security risks.
Avoiding Sensitive Transactions on Public Wi-Fi Networks
It is highly advisable to refrain from conducting sensitive transactions, such as online banking or entering personal information, while connected to public Wi-Fi networks. Hackers can easily intercept this data and compromise your privacy and security.
Role of Secure Website Connections (HTTPS)
Secure website connections, indicated by the HTTPS protocol in the URL, play a vital role in safeguarding user data on public Wi-Fi networks. HTTPS encrypts the data exchanged between your device and the website, making it harder for cybercriminals to intercept and steal sensitive information.
Tips to Enhance Security Posture on Public Wi-Fi Networks
- Avoid connecting to unsecured public Wi-Fi networks and opt for trusted networks whenever possible.
- Enable two-factor authentication for your online accounts to add an extra layer of security.
- Use a virtual private network (VPN) to encrypt your internet connection and protect your data from prying eyes.
- Keep your devices and software updated to patch any security vulnerabilities that hackers could exploit.
- Avoid accessing sensitive information, such as passwords or financial data, while connected to public Wi-Fi.
Final Wrap-Up

As we wrap up our discussion on the security risks of public Wi-Fi networks, it's crucial to remember that vigilance is key in safeguarding your digital presence. By adopting best practices and staying informed, you can navigate the online landscape with confidence and security.
Stay safe, stay secure.
Essential FAQs
What are the most common security risks associated with public Wi-Fi networks?
Common risks include Man-in-the-Middle attacks, Rogue Hotspots, and Packet Sniffing.
How can Virtual Private Networks (VPNs) enhance security on public Wi-Fi networks?
VPNs encrypt your internet connection, ensuring your data remains secure from potential cyber threats.
Why is it important to avoid sensitive transactions on public Wi-Fi networks?
Public Wi-Fi networks are vulnerable to hacking, making it risky to conduct transactions involving sensitive information like banking details.